I didn't like that general users can see the host location of other visitors. So I made a change (TestUser001 is a non-admin testing account).
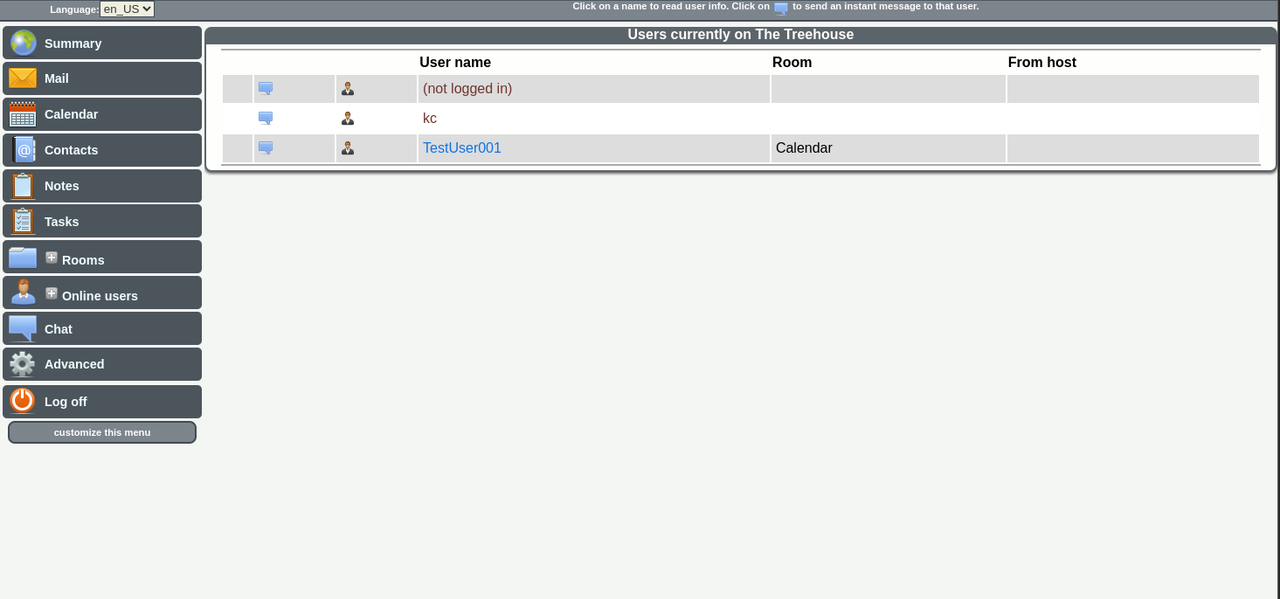
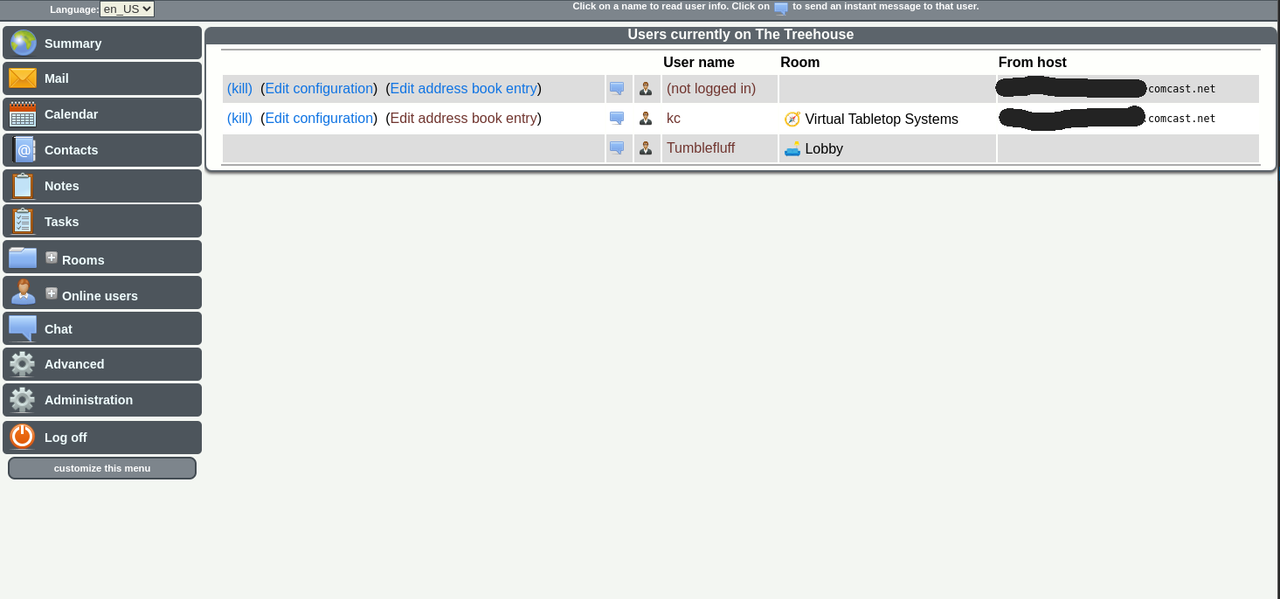
Here's the file and location of what you need to edit
- /usr/local/webcit/static/t/who/section.html
- or - /usr/local/webcit/local.static/t/who/section.html
Here's the contents of the file that rendered the above screenshot.
<tr class="<?ITERATE:ODDEVEN>">
<td class="edit_col">
<??("COND:AIDE", 1)><??("WHO:ISME", 2)>
<a href="terminate_session?which_session=<?WHO:SESSION>?template=who" onClick="return ConfirmKill();"><?_("(kill)")></a>
(<a href="display_edituser?username=<?WHO:NAME("U")>&edit_config_button=Edit+configuration&nonce=<?NONCE>"><?_("Edit configuration")></a>)
(<a href="display_edituser?username=<?WHO:NAME("U")>&edit_abe_button=Edit+address+book+entry"><?_("Edit address book entry")></a>)
<??("X", 2)><??("X", 1)>
</td>
<!-- link to page this user -->
<td><a href="display_page?recp=<?WHO:NAME("X")>">
<img src="static/webcit_icons/essen/16x16/chat.png" alt="(p)" title="chat"></a>
| </td>
<!-- idle flag -->
<td>
<?!("WHO:IDLE", 4)>
<img align="middle" src="static/webcit_icons/essen/16x16/user.png" alt="(<?_("idle since")>s <?WHO:IDLESINCE> <?_("Minutes")>)" title="(<?_("idle since")>s <?WHO:IDLESINCE> <?_("Minutes")>)">
<?!("X", 4)>
<??("WHO:IDLE", 5)>
<img align="middle" src="static/webcit_icons/essen/16x16/activeuser.png" alt="(<?_("active")>)">
<?!("X", 5)>
</td>
<!-- username (link to user bio/photo page) -->
<td>
<a href="do_template?template=user_show?who=<?WHO:NAME("U")>"><?WHO:NAME("X")></a>
<??("WHO:NSESSIONS", 6, 1)>[<?WHO:NSESSIONS>]<?!("X", 6)>\
</td>
<!-- room -->
<td>
<?WHO:ROOM>
<?!("WHO:REALROOM", 7)>
<br><i> <?WHO:REALROOM("X")> </i>
<?!("X", 7)>
</td>
<!-- hostname -->
<td class="host_col">
<??("COND:AIDE", 1)><??("WHO:ISME", 2)>
<?WHO:HOST("X")>
<?!("WHO:REALHOST", 8)><br><i> <?WHO:REALHOST("X")></i>
<?!("X", 8)>
<??("X", 2)><??("X", 1)>
</td>
</tr>
Redacting information for the safety of my visitors. 👍
--
- Tumblefluff the Squirrel
I have a server that seems to be keeping the logs forever, and keeps running out of space. How do I force it to remove the logs once they are committed?
Marisa
Would be better posting this over in the support room, will be more likely to be seen. ( and no, i dont have the answer )
I have a server that seems to be keeping the logs forever, and keeps running out of space. How do I force it to remove the logs once they are committed?
Marisa
Oops! Meant to do that!
I have a server that seems to be keeping the logs forever, and keeps running out of space. How do I force it to remove the logs once they are committed?
Marisa
There is a system setting called "Automatically delete committed database logs" in your global configuration. You can change it from WebCit (administration screen) or from the text client (.Admin System-configuration General). Set it to "Yes" to make Citadel Server purge database log files that are no longer needed.
This is also the default setting.
Nice little hack.
Granted WebCit is on the way out, I do feel in the interim something to this effect might be nice in release as a default.
Still, if memory serves that information would still be present via a Who lookup on the text client, so it's still not a complete obfuscation...
Hello, I setup my own mailserver and its kinda weird how its setup but ill try to explain. I have a mailserver at mail.domain.com and its sending mail for my domain domain.com. The server is self hosted and a PTR record for my IP is set to the ISP's domain but that domain is pointed to my IP which makes my email panel accesible via the ISP's domain the only issue is that im receiving a 550-5.7.25 error. Can someone help me setup the right DNS records?
My current DNS records are:
mail.domain.com. 1 IN A !MYIP!
domain.com. 1 IN MX 10 mail.domain.com.
domain.com. 1 IN TXT "v=spf1 ip4:!MYIP! -all"
and when I run dig on my IP
!ReversedIP!.in-addr.arpa. 86400 IN PTR !ReversedIP!.ISP.com
And some DMARC and domainkey records
hi,
the conftests in version 1001 (and likely all previous ones as well) need an upgrade. they fail with compilers which default to c99 due to formalities and hence the actual check fails even if it would actually pass.
conftest.c:25:3: error: type specifier missing, defaults to 'int'; ISO C99 and later do not support impli
cit int [-Wimplicit-int]
25 | main() {
| ^
| int
conftest.c:29:4: error: call to undeclared library function 'exit' with type 'void (int) __attribute__((n
oreturn))'; ISO C99 and later do not support implicit function declarations [-Wimplicit-function-declarat
ion]
29 | exit(0);
| ^
conftest.c:29:4: note: include the header <stdlib.h> or explicitly provide a declaration for 'exit'
skeleton so far:
main() {
exit(0);
}
should be:
#include <stdlib.h>
int main() {
exit(0);
}
Dear All,
1st I had to delete or move (to a local folder (Thunderbird)) 2 months of sent and received emails. I done such operation with Thunderbird.
2nd The data folder (/usr/local/citadel/data) had 2.6GBytes occupied.
3rd With that operation many log files were generated and the disk became full (about 9 GBytes in data folder). Citadel became unusable. I used a old data backup to recover.
Could you provide a solution for this do not happen again? Perhaps do not generate the log files.
Thanks for the support that will be provided,
Luís Gonçalves.
Hi,
I've just set up Citadel on 2 VPS servers after years of dicking around with Postfix, Dovecot and MySQL.
I'm baffled as to how to set up for users with different domains.
If I have 4 domains, xyz.com, fxy.com, zfx.com and zyy.com, how do I configure email user accounts for them? If I have 4 guys called dave and each of them has an account at each domain, how do I set it up?
Many thanks,
Dave Coventry
Subject: Re: How do I configure users on different domains?
I'm baffled as to how to set up for users with different
domains.
Very easy: you just give them email addresses in different domains.
Their account names in Citadel have to be different, of course. But you could for example have a Citadel user called "John Doe" with an email address of john@example.com , and another Citadel user called "John Deere" with an email address of john@tractors.net , and Citadel will handle them as you expect.
Obviously, all of those domains need to be configured in your server as local domains.
the conftests in version 1001 (and likely all previous ones as
well) need an upgrade. they fail with compilers which default to
c99 due to formalities and hence the actual check fails even if
it would actually pass.
I see you also posted to the development room -- I'll answer this there.
Subject: Re: How do I configure users on different domains?
Thanks.
Clearly, the user names have to be diffierent on Citadel.
Previously, I had dave@xyz.com as the username, but Citadel removes the @sign.
My users all currently have their full email address as their username. Is there any way to do this?
Dave Coventry
Subject: Re: How do I configure users on different domains?
Dear All,
1st I had to delete or move (to a local folder (Thunderbird)) 2 months of sent and received emails. I done such operation with Thunderbird.
2nd The data folder (/usr/local/citadel/data) had 2.6GBytes occupied.
3rd With that operation many log files were generated and the disk became full (about 9 GBytes in data folder). Citadel became unusable. I used a old data backup to recover.
Could you provide a solution for this do not happen again? Perhaps do not generate the log files.
Thanks for the support that will be provided,
Luís Gonçalves.
Subject: Re: Could you please answer to this post? Thanks.
there was a similar question in an earlier thread, which had a solution. i have not found it yet. but i do believe it was in this room a couple of weeks ago.